Two-factor authentication (2FA) adds an extra layer of protection to the login process. In addition to the standard login, 2FA utilizes a Time-based One Time Password (TOTP) calculated password from the user.
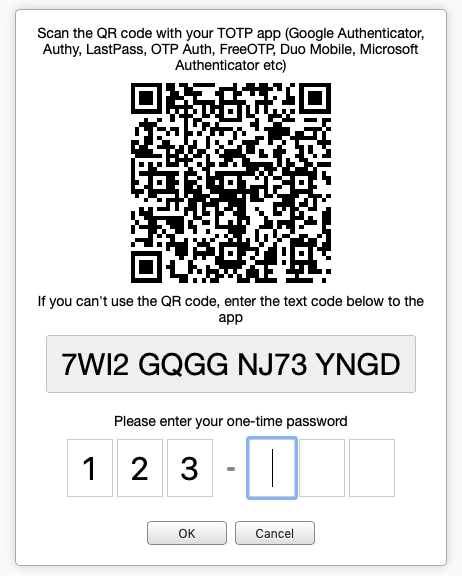
When two-factor authentication is enabled in myDBR, and the user logs in, myDBR checks whether the user has activated 2FA by registering the QR code on their device, typically a smartphone. The user registers with the QR code/token, and the secret value is stored both on the device and in myDBR. This secret value serves as the basis to calculate the time-based one-time password.
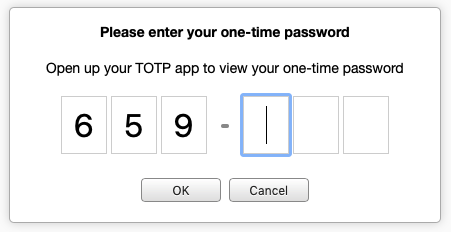
When a user with completed 2FA setup logs in, they are prompted for the time-based one-time password.
The secret value for a user can be reset from the admin's user list. If the admin loses their secret, preventing login due to 2FA, the secret value can be reset by removing the admin's row from the mydbr_twofa_secrets table.
As TOTP is a standard (RFC 6238), there are plenty of apps to choose from. Here is a list of a few common ones:
- Google Authenticator
- Authy
- LastPass
- OTP Auth
- FreeOTP
- Duo Mobile
- Microsoft Authenticator
2FA can be limited to external IP addresses and/or restricted to admin accounts only. This way, one can require the use of 2FA when the user is accessing the system from outside the internal network or limit it to admin accounts, providing additional security for administrators.